本文是其中的一部分TechXchange:网络安全
正如目前正在获得大量新闻的医院和工业系统的全球攻击所证明,使用赎金软件攻击的系统数量正在上升。有问题的攻击使用基于Wannacry的Wannacrypt Ransomware。它带来了一个好问题:勒索软件和恶意软件之间有区别吗?
简单地说,勒索软件是恶意软件的子集。恶意软件攻击通常以计算机病毒或蠕虫的形式出现。对文件,电子表格或电子邮件等类似的病毒背驮式,而蠕虫是一个更积极的攻击。它从网络计算机系统开始,并尝试颠覆一个或多个网络上的计算机。当网络计算机的数量和连接有限时,这曾经很困难。这些天,当然,互联网有效地联系了数十亿个设备。
Present-day malware typically consists of a combination of one or more viruses and worms. This allows the malware to remain hidden and spread itself among files on a host computer, as well as spreading to other computers. Malware tends to be specific to a platform like Windows, or even an application. This allows the malware to target specific security holes or improperly configured systems.
Ransomware differs primarily in its approach after a successful attack. Non-ransomware malware may simply be annoying or slightly malicious, deleting files or changing the system configuration (e.g, a screen background). More malicious malware may reformat a disk or corrupt files on the system. It may also remain hidden and communicate with a control system so it can be part of a distributed denial of service (DDOS) attack. In addition, malware may try to capture information from passwords and keystrokes to documents, and then forward this information to a control system.
当恶意软件通知系统的用户已被攻击时,赎金软件发挥作用,但在它对计算机上做了什么之后,例如加密磁盘或文件。该通知通常要求将计算机恢复到其先前状态的某些付款。
从理论上讲,管理赎金软件的攻击者将在完成付款后远程重新调整计算机。当然,就像在传统的赎金一样,他们可能不会。
Following the money is how a conventional ransom attack is often traced back to the perpetrator. Doing so is a bit more difficult these days, however, as most ransomware attackers now ask for payment using cypto currencies like Bitcoin (see “What’s the Difference Between Blockchains, Cryptocurrency, Audit Trails, and Databases?” on electronicdesign.com). Delivery often takes place through a communication system that keeps users anonymous.
The WannaCrypt attack encrypted files on a Windows computer and then demands a ransom payment of $300 in Bitcoins. If this is not done within three days of the initial attack, the amount is increased to $600. This ransomware deletes files on the infected machine if this continues past a week.
Wannacrypt使用服务器消息块(SMB)协议中的错误颠覆Windows计算机。Microsoft于3月14日发出MS-17-010安全补丁来解决问题,但系统需要安装要保护此更新。通常,Wannacrypt需要通过其他方式到达,因为大多数SMB网络将在防火墙/网关后面。当然,直接连接到互联网的错误配置的计算机也会易受影响。
WannaCrypt is just one example of ransomware, albeit a notable one that has affected tens of thousands of computers (primarily in Europe, although it reach is worldwide). Also of note is that it asks for small amounts of money, and has a kill switch—the latter was discovered by a researcher; otherwise it may have spread wider that it already has.
One way to recover from this type of ransomware attack is to resort to backups, if they exist. Unfortunately, many do not have backups that are isolated from the host computer. Backups stored on a disk attacked to a compromised computer would be under attack, as well.
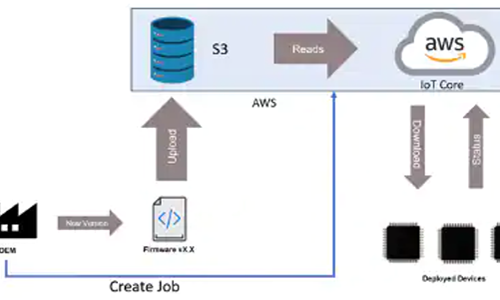
Ransomware should be of particular concern to embedded developers, since this type of attack is not limited to workstations or servers. In fact, many embedded systems already run Windows. Embedded systems often have additional challenges because the update process may be restricted due to one or more considerations. For example, medical systems often require certification that prevents arbitrary updates to be applied. Many of the attack vectors for these systems are often discovered after these restrictions are put in place.
开发人员需要意识到与vannacrypt相关的小赎回只是一个开始。通过赎金软件损害数百个昂贵的设备或数百万廉价的设备,可能导致销售或管理如此大集合的公司的重大赎金。甚至可能仅通知与这些受损设备相关联的公司,同时保留在黑暗中的设备所有者。
Still, preventing ransomware attacks is no different than preventing security breaches in general. It means implementing proper security measures as well as minimizing bugs—or, hopefully, eliminating them all. Remote updates can help assuming fixes can be deployed before bugs can be exploited.
最后一个注意事项:请记住,即使系统使用安全启动,Wannacrypt也有效。这是因为问题发生在安全软件中。
Read more articles at theTechXchange:网络安全