This article is part of theCommunicationSeries:加密技术手册
Let’s recap some of the basics we’ve learned so far from our series and then review how we can use what we’ve learned. Along with a few well-designed secure authenticators, we’ll show how to utilize them in some amazingly simple but very secure real-life solutions.
Four Essential Goals of Cryptography
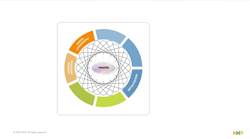
As we learned in thefirst article in the series, the four essential goals of any good cryptographic system are confidentiality, authenticity, integrity, and non-repudiation(Fig. 1). A broad spectrum of secure authenticators and coprocessors, which can help a busy developer quickly implement a secure system, are currently available from various manufacturers.
这些未ocessors essentially unload the cryptographic computation and data-handling requirements from the host microcontroller and seamlessly integrate with the coupled secure authenticators that provide the main security functionalities. Let’s explore a couple of these coprocessors.
Using a Symmetric Key Coprocessor
You’re a developer trying to implement a secure system in a unique gadget that you‘ve created, and the success of your business model perhaps relies on the sale of high-volume consumables or disposables. In this model, you sell a permanently deployed host system to a customer and then they purchase the consumables from you and you alone. This gadget could be a medical consumable or a printer cartridge, where your system performance depends on the disposable peripheral to which it’s connected.
For a medical consumable such as a disposable sensor or tool, the main issues are quality, safety, and use management. For something like a printer cartridge, issues like host-printer damage from poor-quality counterfeits and/or poor-quality print output must be addressed. In both cases, there’s a loss of revenue associated with counterfeit disposables that results in a breakdown of your business model.
So, you need to make sure that the gadgets connected to your main system are authentic and identifiable by your system. This can easily be achieved using secure authenticators such as theDS28E50DeepCover secure SHA-3 authenticator with ChipDNA and its companionDS2477DeepCover secure SHA-3 coprocessor with ChipDNA PUF protection.Figure 2shows a simplified system architecture for this type of cryptographically secured system.
In this system, you attach your favorite microcontroller to the DS2477 and let it handle all of the identification and authentication tasks. It also provides the proper electrical signal strengths and timing to drive the DS28E50s situated in each of the gadgets.
The DS2477 is designed to be very flexible and allows greater control. If you want to dig deep and control all aspects of the cryptographic authentication process, it has low-level commands that will let you do exactly that. But if you want it to handle the complexities for you, it has very high-level commands that allows more hands-off ability toward securing your gadget.
Both the DS2477 and the DS28E50 have built-in ChipDNA PUF features to secure your data with a key that hasn’t been saved physically in the device, but is derived each time it’s needed. This technology was covered in aprevious article in our series.
Using an Asymmetric Key Coprocessor
As was discussed inanother series article, there are instances when the system requires the use of asymmetric keys to secure a system. This is essential to achieve full cryptographic system integrity and non-repudiation.图3illustrates this type of system.
Here, just as before, you need to secure your gadget. However, you want to use a public/private key combination to achieve your cryptographic goals.图3shows theDS2476DeepCover secure coprocessor as the cryptographic helper that has a set of built-in tools to carry out asymmetric Elliptic Curve Digital Signature Algorithm (ECDSA) as well as symmetric SHA-256 functions, both of which were covered in aprevious article. The DS2476 also has a NIST-compliant random number generator that can be used by the host microcontroller to generate the nonce required to prevent “man-in-the-middle” attacks.
In the system shown in图3, the DS2476 and theDS28C36devices (DS28E83/DS28E84are good for radiation-hardened medical applications) work in tandem to secure a new design from counterfeiting and other malicious intents.
Factory Personalization/Pre-Programming Custom Data
Now comes the last piece of the puzzle to easily and quickly implement a cryptographically secure system using secure authenticators. This includes using a Personalization/Pre-Programming service that’s tailored for factory production. This service personalizes or pre-programs your authenticators and coprocessors at the device manufacturer’s facility with either your private or public data. Example data can be a symmetric key/secret or an asymmetric key certificate. An example of the personalization process flow is shown inFigure 4.
这种个性化服务帮助卸载旧姓的d to program the required data to the authenticators in the production settings. In most cases, a manufacturer will need to develop their own test systems and infrastructure to accomplish this task, which can be time-consuming and very costly. Maxim Integrated has provided this service for decades for a wide variety of customers, helping to safeguard their data.
The process begins when the customer requests and then securely transfers the required data to Maxim. This is shown in the first two sections ofFigure 4, where the customer securely inputs data into the Maxim tool in their facility. Once that’s completed, the tool encrypts the data and then it’s sent to Maxim. At this point, Maxim takes over and completes the sample generation process(Fig. 4, again).
Once the samples are approved by the customer, that customer’s part goes into production. From then on, a “ready-to-use” part is shipped to the customer by request.
Conclusion
In “加密技术手册,” we covered the basics of cryptography starting with a general overview and then defined the characteristics of a secure cryptographic system. We described the details of various cryptographic concepts such as encryption and symmetric/asymmetric cryptography. We then provided an overview of various cryptographic algorithms such as SHA, ECDSA, AES, 3DES, and RSA.
Next, we provided an implementation-centric explanation of physically unclonable functions. We hope that this approach gives the busy engineer a quick understanding of why these features are essential for target applications.
After outlining and discussing basic and detailed cryptographic concepts, we showed examples of how those concepts can be used for real-life applications, such as secure boot or IP protection. Lastly, some very important features of the latest secure authenticators and coprocessors were reviewed, as well as a personalization/pre-programming service. We believe that secure authenticators can help an engineer quickly develop and deploy a cryptographically secured system with a very high degree of confidence.
Read more from theCommunicationSeries:加密技术手册
Zia Sardar is an Applications Engineer atMaxim Integrated.